In today's world, where security threats can undo years of hard work in a flash, being cautious is no longer just an option – it's a necessity. Whether you're leading a big company or a small business, ensuring the safety of your workplace is essential.
This article is your ultimate guide to understanding and implementing the ins and outs of office security management. Brace yourself for the must-have checklist that will fortify your workplace security.
TL;DR:
- Workplace security is crucial today due to potential threats that can undermine achievements, making caution a necessity.
- Workplace security involves comprehensive measures for the safety of individuals, assets, and information, covering physical and digital aspects, protocols, and training.
- Robust workplace security provides physical protection, fosters a positive atmosphere, safeguards data and assets, deters unauthorized activities, boosts employee confidence, and ensures emergency preparedness.
- The workplace security checklist comprises risk assessment, a comprehensive security plan, employee protocols, data and technology security, operational procedures, emergency protocols, and testing and reviewing measures.
- Taking a proactive stance on workplace security involves staying ahead of potential threats, fostering a security-focused organizational culture, communicating clear safety rules, limiting access privileges, responding rapidly to risks, and collaborating with local law enforcement. Continuous review and adaptation are essential for maintaining a safe working environment.
What Is Workplace Security and Why Do You Need a Workplace Security Checklist?
Workplace security is the comprehensive measures and strategies implemented to ensure the safety and protection of individuals, assets, and information within a work environment. It encompasses various aspects, including physical security (access control and surveillance), digital security (data protection and cybersecurity), and the development of protocols and training to address potential risks or emergencies. Workplace security aims to create a secure and conducive environment for employees to work without undue disruptions, safeguarding both people and assets from potential threats.
Therefore, a workplace security checklist is essential as it is a practical tool to systematically assess and address specific security measures, helping organizations identify vulnerabilities, implement preventive measures, and ensure ongoing adherence to security protocols. It provides a structured approach to managing security risks and contributes to the overall effectiveness of a comprehensive workplace security strategy.
Understanding the Importance of Security in the Workplace
Recognizing the significance of security in the workplace is crucial for fostering a safe and productive environment. Without adequate security measures, a business exposes its resources and reputation to potential harm. In fact, global cybercrime damage costs are projected to reach USD 10.5 trillion annually by 2025!
The benefits of robust workplace security include:
- Physical Protection: Security measures protect employees, visitors, and assets.
- Positive Atmosphere: A secure workplace promotes a positive and stress-free atmosphere, enhancing the overall work environment.
- Data and Asset Safeguarding: Workplace security measures extend to the protection of sensitive data and digital assets, minimizing the risk of unauthorized access or theft.
- Deterrence: Access controls and surveillance systems deter unauthorized activities, reducing the likelihood of theft or vandalism.
- Employee Confidence: A secure workplace instills employee confidence, boosting morale and overall job satisfaction.
- Emergency Preparedness: Security protocols contribute to emergency preparedness, ensuring a swift and organized response to unforeseen incidents.
The Impact of a Security Breach on Your Business
The consequences of a security breach for a business are profound, encompassing various dimensions that leave a lasting impact:
Financial Toll:
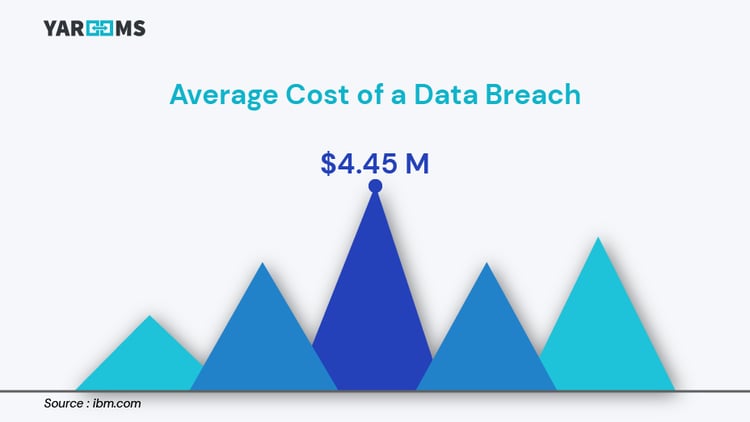
- The average cost of a data breach in 2023 reached a staggering $4.45 million, as reported by IBM's Cost of Data Breach Report.
- Organizations face additional costs, including compensating affected customers, incident response efforts, breach investigations, investments in new security measures, legal fees, and regulatory penalties. Non-compliance with GDPR can result in fines of up to 4% of annual global turnover or €20 million, whichever is greater.
Reputational Damage:
- Up to a third of retail, finance, and healthcare customers may cease business with breached organizations, emphasizing the severe impact on customer trust.
- Reputational damage is long-lasting, with 85% of affected customers sharing their negative experiences and 33.5% expressing their grievances on social media.
Operational Downtime:
- Business operations experience significant disruption, with the aftermath of a breach demanding containment efforts and extensive investigations.
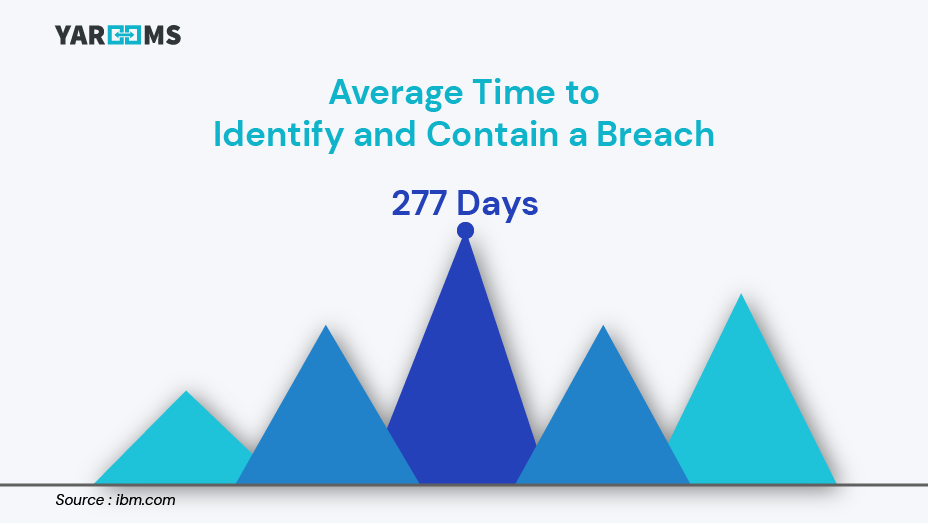
- The average time to identify and contain a breach is 277 days, leading to operational downtime that can substantially impact revenue and recovery efforts.
Legal Implications:
- Legal consequences arise as organizations are legally bound to demonstrate efforts to protect personal data under data protection regulations.
- The rising frequency and severity of data breaches are expected to result in more group cases brought to court, seeking compensation for the consequences of a breach.
Sensitive Data Loss:
- If a breach results in the loss of sensitive personal data, the consequences can be devastating, extending beyond financial and reputational damage.
- Sensitive data, including biometric or genetic information, can profoundly impact medical treatments and patient outcomes and exacerbate the fallout from a breach.
These consequences underline the critical need for a coordinated security strategy to protect data privacy, mitigate threats, and safeguard a business's reputation. In today's dynamic cybersecurity landscape, organizations must remain vigilant and prioritize comprehensive security measures to navigate the multifaceted impacts of a security breach effectively.
Workplace Security Checklist: A Complete Guide to Protecting Your Business and Employees
By following the workplace security checklist, you're not just ensuring peace of mind – you're taking proactive steps to protect your organization from potential issues. In the following chapters, our 8-step checklist will help you address key security measures and ensure your workplace is ready to tackle various threats and challenges.
#1: Conducting a Risk Assessment
When discussing workplace security, it's crucial to consider the importance of a security risk assessment. This essential process involves proactive planning to ensure the safety of people and assets within your organization:
- Identify Assets: First up on any workplace security checklist is identifying what needs protection—perhaps your expensive equipment or sensitive data residing on-site.
- Evaluate Current Measures: Scrutinize policies and deterrents, such as surveillance systems and access control mechanisms.
- Threat Identification: Analyze potential threats specific to your industry or location, ranging from theft and sabotage to natural disasters.
- Risk Evaluation: Using the collected information, assess each identified risk based on its potential impact and likelihood.
- Prioritize Risks: Rank risks according to severity, laying the ground for remedial actions, with the most pressing ones receiving immediate attention.
- Review and Modify: Threats keep evolving with time. Review your list for any updates or revisions needed to maintain safety standards.
#2: Establishing a Comprehensive Workplace Security Plan
The backbone of any security measure in the workplace is a comprehensive plan. By creating an effective strategy, you directly tackle potential vulnerabilities to ensure your business's and your employees' safety.
Developing Clear Policies and Procedures
Start making your workplace more secure by setting up clear, straightforward rules and procedures that match your organization's security goals. These rules act like a roadmap, showing what's okay and what's not in the workplace. They give a solid foundation for quick decisions when situations or threats arise.
By laying out expectations and ways to respond, these rules make it easier to manage security smoothly and organized. It's super important to ensure everyone on your team understands these rules well. This helps create a culture where people are aware of security and gives them the power to be proactive in spotting and dealing with possible security issues.
Sharing this knowledge about the rules goes a long way in boosting workplace security, making everyone feel responsible and watchful. Being proactive like this is vital to keeping the place safe and handling potential problems effectively.

#3: Setting Up Employee Protocols for Ensuring Workplace Security
One of the pillars of workplace security awareness is bringing employees on board by designing and implementing fitting protocols. Knowledgeable and informed employees play a significant role in preventing security breaches, whether physical or digital.
Training Employees on Security Awareness and Threats
An investment in knowledge pays the best interest. Central to fostering workplace security awareness is employee training. Regular seminars can acquaint workers with common security threats like phishing emails, malware infections, or tailgating attempts. Mock breach scenarios offer practical experience, reinforcing theoretical knowledge. Tailoring content to your industry sector's examples makes potential risks more tangible. Well-informed employees with up-to-date knowledge become your first line of defense against malicious actors.
Encouraging Reporting Suspicious Activities or Behaviors
A secure workspace needs an environment where employees can confidently report suspicious activities. Beyond merely recognizing incidents, it's essential to establish a transparent reporting process: define suspicious behavior, set procedures for recording and escalating incidents, and provide confidential avenues for alerts such as hotlines and anonymous tip boxes. Most importantly, cultivate a no-blame culture that encourages reporting without fear of retribution.
Ensuring Proper Badge and Token Usage
The widespread use of badges and tokens in workplace access systems emphasizes the need for clear protocols to ensure proper usage, forming a crucial aspect of workplace security. Observing critical rules is paramount:
- Wear badges visibly in secured areas.
- Refrain from lending tokens or sharing PIN codes.
- Promptly report lost or stolen badges to prevent unauthorized access.
Maintaining a secure working environment is a collective responsibility. Providing training, fostering open communication, and adhering to protocols significantly reduce security risks. Despite their apparent simplicity, the full implementation of these employee protocols distinguishes between a vulnerable workspace and a well-protected fortress.
#4: Implementing Data and Technology Security Measures
Rapid technological advances make protecting data and computer systems more critical than ever. An essential part of your workplace security checklist should be appropriately securing your technology stack, including computers and all devices connected to the network.
Securing Computer Systems with Firewalls and Antivirus Software
Firewalls are integral to any security checklist because they act as the primary defense against malware attacks, unwanted traffic, or intrusion attempts. Installing a robust firewall system can thwart potential invaders from infiltrating our network.
Equally essential is antivirus software that detects noxious files before they can infect our system. Viruses often masquerade as legitimate applications or documents; hence, having functional antivirus software significantly reduces the odds of inadvertently downloading malicious content.
Establishing User Access Controls and Password Policies
User access management involves dictating what information each employee can access within your IT infrastructure. By employing stringent user access controls, we limit exposure to sensitive material solely to those who genuinely need it for their roles.
Similarly crucial on the digital battlefield is creating strict password policies. Encouraging employees to use complex passwords changed regularly can prevent unauthorized users from gaining entry into your systems. Strong passwords should contain a combination of letters (both uppercase and lowercase), numbers, and special symbols.
Protecting Sensitive Data through Encryption and Backups
When we discuss protecting sensitive data, encryption comes at the front-row center. Converting data into codes restricts unplanned access if someone intercepts it during transmission over networks or while stored in databases. Backing data onto secure offsite servers further injects confidence against possible cyber threats or physical damage, such as fires or natural disasters that could devastate onsite resources.
#5: Operational Procedures for Maintaining Workplace Security
When implementing your workplace security checklist, it is essential to establish and maintain effective operational procedures. A comprehensive security plan is only possible with strategic execution.
Establishing Regular Security Inspections and Audits
Regular security inspections keep you aware of your workplace's current status in terms of safety and vulnerabilities. With these inspections, you ensure that every element on the building security checklist is followed appropriately.
Consider performing monthly or quarterly audits depending on the size and needs of your business. Above all, doing this keeps everyone alert about potential threats and encourages a culture of proactive defense against breaches.
Conducting Background Checks for New Hires
Ensuring the trustworthiness of your employees is crucial for workplace security. Conduct thorough background checks during the hiring process to reduce internal risks, especially regarding access to sensitive data and critical infrastructure, which could be misused. The focus is on preventing issues beforehand, as dealing with problems after employment begins can lead to more severe consequences.
Implementing a Solid Visitor Management Policy
Visitors often present unforeseen risks to business facilities as they are less familiar with operational protocols. Establishing visitor policies contributes significantly to job site safety through controlled access and monitored entrances/exits.
A well-thought-out policy starts from arrival until departure, capturing data like visitor details (name, address), purpose & duration of visit, and host details with a modern visitor management system—all crucial in limiting unauthorized access while ensuring guest convenience.
Reviewing and Updating Security Measures as Needed
Apart from routine audits, a reassessment should coincide with significant internal changes, such as restructuring or relocating, and external updates, like changes in local laws. The complexities of emerging technologies require regular reviews, depending on how these technologies are integrated into existing systems or processes in your workplace security plan. Due to the ever-evolving nature of threats, updating security measures regularly is not optional.
#6: Establishing Emergency Protocols for Responding to Security Threats
Emergencies can occur at any time without warning. When they do, your employees' safety and business sustainability may depend on your preparedness and efficiency in response. Dealing with potential security threats in advance requires a committed plan of action.
Developing an Emergency Response Plan
An emergency response plan is a structured procedure manual that outlines how to respond swiftly when crises like natural disasters occur. Here are crucial elements that should be included:
- Identification of potential emergencies
- Outlining responsibilities for team members during crises
- Stipulation of communication processes
- Evacuation routes and procedures
- Enlisting professional contacts (like hospitals or fire departments)
Developing this plan allows businesses to anticipate a possible emergency logically rather than react impulsively when it happens.
Conducting Drills and Training Exercises
While having an emergency response plan on paper is crucial, its success relies on proper execution when needed. To ensure smooth implementation, conduct regular drills that identify system loopholes and familiarize employees with their roles during emergencies. These drills should cover everything from simple instructions to handling panic situations effectively. Regular tabletop exercises also provide chances to assess your team's readiness levels, reinforcing coordinated responses developed through routine drills.
Moreover, everyone in the office must know the location of the fire drill or first aid trained personnel. A desk booking system like Yarooms can help achieve this by displaying employee locations on an interactive floor map.

Collaboration with Local Law Enforcement and Emergency Services
Besides internal preparations, building external partnerships significantly enhances workplace security. Collaborating with local law enforcement, medical services, and fire departments proves highly beneficial. Keeping open communication channels with these institutions ensures a prompt response in emergencies and allows for expert advice to improve security measures based on their crisis management experience. These collaborative relationships also assist in rescues and evacuations when needed, acting as an additional safety net for the organization during unexpected circumstances.
#7: Testing and Reviewing Your Workplace Security Measures
Perfecting the security measures is a continuous process in our quest to secure our workplace effectively. This journey requires a persistent effort in testing, reviewing, and fine-tuning these safety controls.
Regular Testing and Evaluation of Security Systems
Regular testing ensures that every aspect of our pre-established security systems functions as planned. Scheduling periodic checks on all access controls, surveillance equipment, alarm systems, and computer software protection mechanisms like firewalls or antivirus programs helps identify faulty areas needing immediate attention or repair.
It's also beneficial to conduct unannounced tests occasionally to gauge how well your business responds realistically to unexpected security threats. These spot checks often accurately measure vulnerability in real-life crisis situations.
Internal and External Audits to Identify Weaknesses
Surprisingly, our daily operations may unintentionally create vulnerabilities in our defense strategy, highlighting the need for thorough audits. Internal audits help us understand how different aspects align with our workflows, identifying potential weak points by comparing practices with industry standards.
External auditing agencies offer an unbiased perspective based on their expert insights from diverse assignments. Combining internal and external audits creates a comprehensive system that addresses weaknesses at various levels within our corporate structures.
Continuous Improvement of Security Practices
Just as Rome wasn't built in a day, achieving top-notch workplace safety requires ongoing improvements. Simply conducting regular tests and detailed audits is not enough; the key lies in implementing improvement suggestions.
Remember to continuously review and update security measures for a safe working environment. Moving forward, undertaking regular tests, comprehensive audits, implementing recommended changes, and promoting a culture of continuous learning and adaptability will create a resilient sanctuary for your workforce's well-being.
#8: Choosing the Right Workplace Security Solutions for Your Business
The art of securing your workplace is a complex yet necessary endeavor. It involves considering various significant variables in keeping your staff and inventory safe. This section aims to provide insights on selecting optimal security solutions for your enterprise, emphasizing the evaluation process of different systems and providers.
Evaluating Different Security Systems and Providers
When selecting a suitable security framework, it's critical to note that not all systems are created equal. Varied mechanisms offer diverse benefits and can significantly differ in functionality, implementation complexities, or even costs.
Investing the time upfront to evaluate these dissimilarities will pay dividends in ensuring you choose an effective solution tailored perfectly to your business's unique needs. Here's how:
- Assess Your Needs: Identify what security aspects you need to improve drastically per your risk assessment findings.
- Research Available Options: Distinguish between nuanced variations offered by systems such as intruder alarms, access control technology, surveillance systems, or cybersecurity software.
- Consider Provider Reputation: Verify each provider's track record within similar industries by reading customer testimonials and checking their credentials thoroughly.
- Examine After-Sale Support: Exemplary post-sale service includes 24/7 technical support, regular maintenance checks, and accessibility when urgent issues arise.
Success lies in adopting exemplary safety measures and partnering with reputable suppliers who can guarantee reliable help when needed most.

Key Considerations for Selecting the Best Solution
Once armed with potential options sourced from rigorous evaluations, deciding on an ultimate selection becomes much more accessible - if you bear some pivotal considerations in mind:
- Scalability: Does the system allow for progressive adaptations should growth occur or threats evolve?
- Integration: Can it integrate seamlessly into current operational procedures without heavily disrupting workflows? How well does it work with any existing security structures?
- Return on Investment: Consider the financial ramifications. Analyze potential cost savings regarding loss prevention, insurance premiums, and reduced risk incidents.
- User Friendliness: User-friendly interfaces promote better adherence to new changes by staff, ensuring consistency in using security features correctly.
Paying heed to these critical aspects can transform overwhelming choices into a straightforward selection. In turn, you will bolster your defense against relentless modern-day risks that threaten businesses globally.
Wrapping Up: Proactive Approach to Workplace Security
Taking a proactive stance on workplace security is crucial for safeguarding your business assets. Being proactive means staying ahead of potential threats, fostering a security-focused organizational culture, and integrating technology advancements. Communicate clear safety rules, limit access privileges, respond rapidly to risks, and collaborate with local law enforcement.
Workplace security is not foolproof, so continuous review and adaptation are essential for maintaining a safe working environment. A ceaselessly proactive approach signals your commitment to security, ultimately protecting and propelling your business forward.